Monday, 20 June 2016
Sunday, 19 June 2016
Internet of Things IoT - Augmented Reality - Very Interesting but too dangerous - Leads to Virtual Life
Yesterday I have attended a training for IoT - Internet of Things. It was very interesting. World is growing very fast. In near future our world is connected via IoT. It is sure, IoT will replace our mobile phones and people will speak with each other through Augmented Reality. Every human, pet animals, home, office will be addicted to IoT. But....
What will happen in future?
What will happen in future?
- Every human will have one address just like IP address or MAC address even other organisms.
- Human name will be assigned to IP address just like in DNS server.
- We can easily ping any persons in the world.
- We can identify whether that person is live or dead(shutdown) :-)
- We can identify unknown persons name, address, what diseases he/she is having, in which company he/she is working, married or not, crime record, friends details, mutual friends, etc.
- No need to book tickets to go our native or distant places.
- Without travelling we can enjoy the world's nature.
- We can easily climb Mt Everest.
- We can visit Artic and Antartic continent within a minute.
- Just a like a video game, our life will be changed.
- Even if we dead, we will have more life chances by earning points.
- We will visit all temples virtually, (already started online temple visits in many countries).
- People no need to learn other languages rather just think in native language, some device will translate and other person can understand.
- There is no real love between each others.
- Virtual Love replaces Real True Love.
- We are going to live Virtual Life - already many people started.
- And finally we will get baby virtually and virtual baby grows within a second - Virtual Population will grow rapidly and Real Population will be drastically reduced by this way.
- Do we need this?
Monday, 6 June 2016
My first publication - "Hacking Tools" is live on Amazon today - 06-06-2016
My first publication - "Hacking Tools" is live on Amazon today.
https://www.amazon.com/
https://www.amazon.in/Hacking-Tools-Saravanakumar-H-ebook/dp/B01GN57HCE?ie=UTF8&keywords=hacking%20tools&qid=1465188030&ref_=sr_1_11&sr=8-11
I encourage you all to use this tools only for educational purposes and please do not misuse the tools. Without prior permission from clients, please do not use this tools.
The main intention of this book publication is to collect some money and spend for poor child education. And I promise to dedicate 100% money except tax will be spend for poor child education.
Regards,
Saravana
https://www.amazon.com/
https://www.amazon.in/Hacking-Tools-Saravanakumar-H-ebook/dp/B01GN57HCE?ie=UTF8&keywords=hacking%20tools&qid=1465188030&ref_=sr_1_11&sr=8-11
I encourage you all to use this tools only for educational purposes and please do not misuse the tools. Without prior permission from clients, please do not use this tools.
The main intention of this book publication is to collect some money and spend for poor child education. And I promise to dedicate 100% money except tax will be spend for poor child education.
Regards,
Saravana
Sunday, 22 May 2016
Serial Peripheral Interface - SPI
Introduction:
SPI allows full-duplex, synchronous, serial communications with peripheral devices. Software can either poll the SPI status flags or SPI operation
can be interrupt driven.
Features:
- Communication between SPI and external device is always synchronous.
- SPI is interfaced with external peripheral device for data transfer.
- SPI can transfer data to an external peripheral device.
- SPI can receive data from an external peripheral device.
- SPI can work in master or slave mode.
- In master mode, SPI clock drives the slave peripheral.
- In slave mode, the external clock drives SPI.
SPI Interfacing with a device:
MOSI:
Master
Out Slave In - Output from SPI, connected to Serial Data Input of the peripheral
device.
MISO:
Master
In Slave Out - Input to the SPI, connected to Serial Data Output of the peripheral
device.
SCLK:
Clock
output from the SPI to the clock input to slave.
SS:
Chip select output from the SPI - master selects the chip with
which it wants to communicate.
Single master, single slave SPI implementation:

Single master, multiple slave SPI implementation:
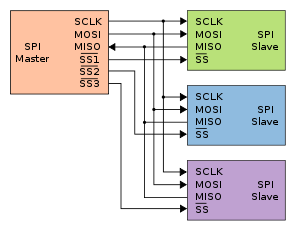
Data Transfer mechanisim:
- The software module begins an SPI transmission by writing a byte to the SPI transmit data register.
- This byte is transferred to the shift register, when SPI transmit data register becomes empty the byte begins shifting out a bit at a time on the MOSI pin synchronized with the master clock signal.
- The transfer will continue for 8 clock cycles, transferring all 8-bits.
- The transmission ends when the whole byte is shifted out of the master SPI shift register and into the slave shift register.
- If SPI is receiving, the incoming byte will come to the shift register from the MISO pin.
- When one complete byte is received by the shift register, byte is copied to receive data register.
Thanks for reading !!!
All the Best !!!
Regards,
Saravana
Subscribe to:
Comments (Atom)

